Transilience Managed Compliance service offers compliance outcomes that includes
- Security monitoring, incident creation
- Vulnerability management, prioritization
- Standards check, against CIS
- Pen testing
- Risk analysis, risk acceptance
- Access reviews, network access reviews, log reviews
There are two documents , one for giving access to subscriptions and second to give access to logs and active directory.
This current document explains how to give permissions to Transilience backend to access your Azure subscriptions and read configurations needed for the audit. If you are using Azure Entra ID for users, Azure Intune for audit logs, please refer to on boaring logs document for giving us access to verifying log and AD configurations. We need access to both subscriptions and logs for complete configuration audit for compliance.
There are two to the process of giving access to subscriptions, step 1 is to add an app , and step 2 is to add permissions to the app to collect the configuration.
Step 1. Add app and permissions
1.1 Add app registration on the app registrations page

1.2 Register tha app

1.3 Add client certs

1.4 Create a new client secret

Copy the Application (client) ID, secret value and secret ID (along with tenant ID and subscription ID). You need to send it to us after you assign permissions below.
Step 2 . Assign Permissions
Once the app is created, you need to add the permissions for the app to read configuration.
** you need to add permissions in each of the subscriptions, you would need user administrator role to add permissions **
2.1 Go to the subscription, and IAM

If not already, activate reader permissions

2.2 Add Role Assignment


2.3 Click select members link, find the app name and add

2.4 Select Reader Role

2.5 Add Reader and Data Access permissions as well

2.6 Add Sentinel Roles (if logs are stored on Microsoft Sentinel)
We would need Sentinel Reader and Log Analytics Reader roles.
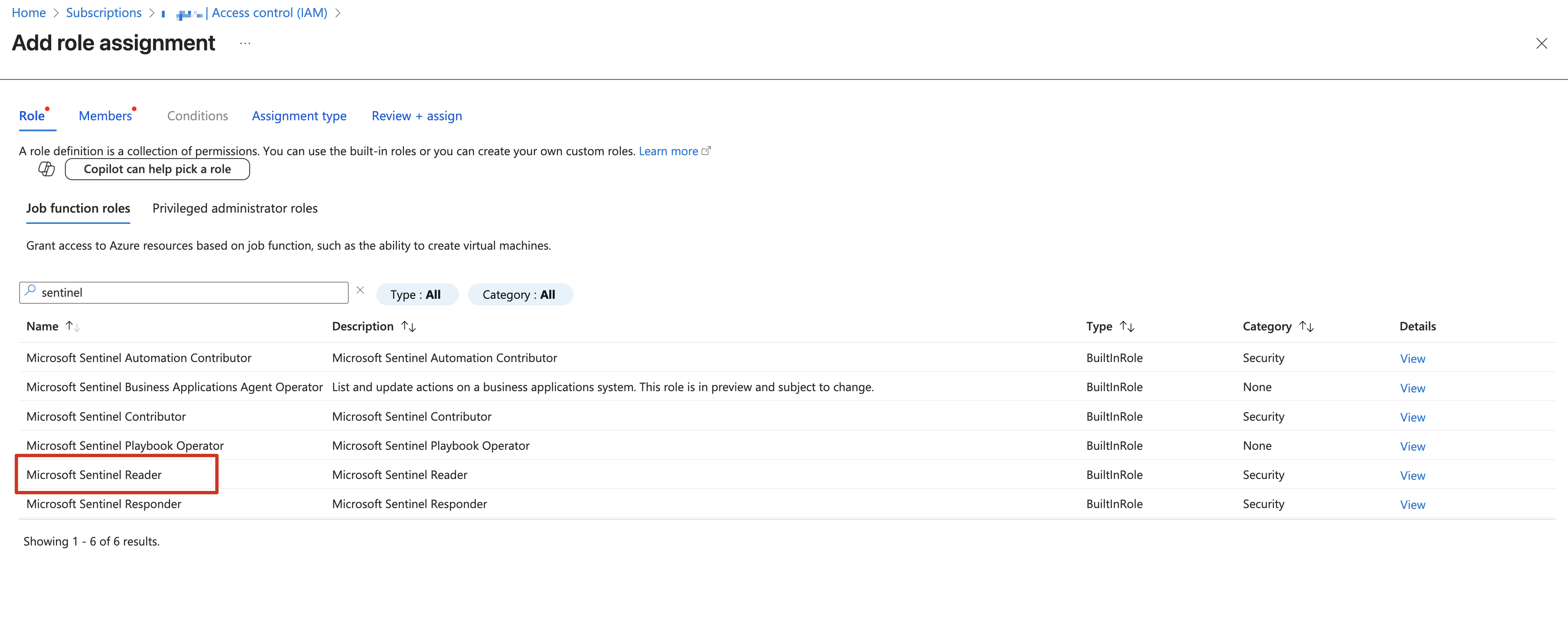
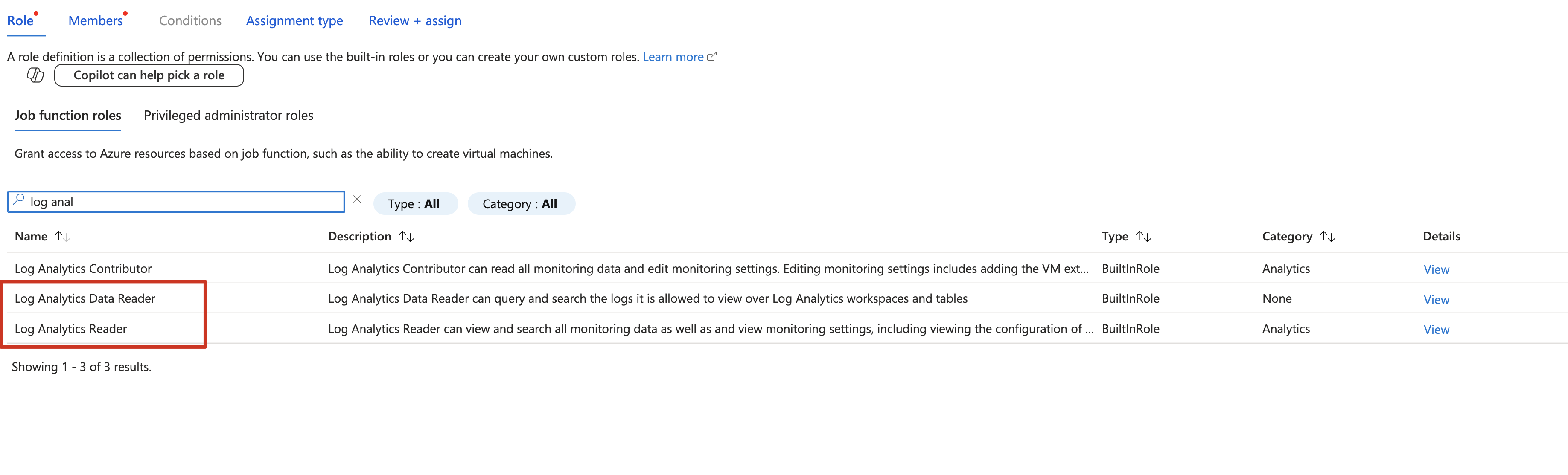
2.6 Review and assitgn

2.7 Note the subscription ID and Tenant ID
Subscription ID should be on the subscriptions page and tenant ID is on tenant properties page
-subscriptionid
- tenantid

Note : If you are using Azure Entra ID for users, Azure Intune for audit logs, please refer to this document for giving us access to verifying log and AD configurations.
Last step
Send the client ID, secret value, secret ID, subscription ID and tenant ID to your account manager
Was this article helpful?
That’s Great!
Thank you for your feedback
Sorry! We couldn't be helpful
Thank you for your feedback
Feedback sent
We appreciate your effort and will try to fix the article